Apache Ranger KMS
Cryptographic Key Manager

A cryptographic key manager (KMS) is a solution or service designed to manage and protect encryption keys used in data and communications security. They play a crucial role in ensuring the confidentiality and integrity of sensitive data.
The idea of managing cryptographic keys dates back to the early days of cryptography, but the term "KMS" became more relevant with the increased use of encryption technologies in enterprise environments.
Among its relevant features, we highlight:
- Secure key storage: KMSs keep cryptographic keys in a highly secure environment, such as Hardware Security Modules (HSMs) or encrypted software;
- Key generation: They can create strong and random cryptographic keys;
- Key distribution: KMSs securely distribute keys to systems and applications that need them;
- Access control: They allow strict control over who can access and use the keys;
- Auditing: They record key-related activities for auditing and compliance purposes;
- Security policies: They allow the enforcement of security policies, such as key rotation and key expiration.
The architecture of a KMS varies, but generally consists of a central key management component, a secure key repository, and access control mechanisms. HSMs are often used to store keys securely, protecting them from unauthorized access. Security policies are applied to determine who can access and use the keys.
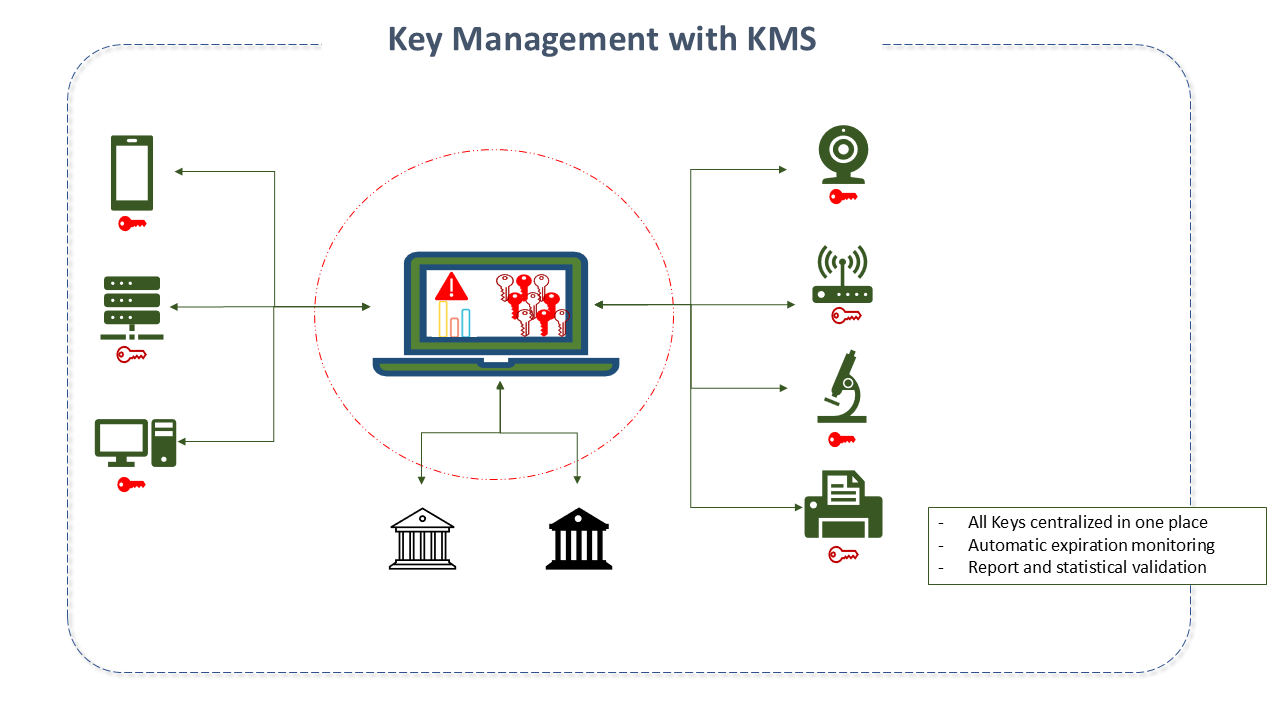
Main Types in the Market:
- HSMs (Hardware Security Modules): Dedicated physical devices for storing and managing cryptographic keys in a highly secure way;
- Cloud KMS: Cloud-based services that offer key management as a service, such as AWS Key Management Service (KMS) from Amazon Web Services;
- On-Premises KMS: Software solutions that can be deployed on local infrastructure or in private cloud environments;
- Third-Party KMS: Many security vendors offer their own KMS solutions for use in conjunction with their products.
KMSs are essential to ensure the security of sensitive data, protecting encryption keys against internal and external threats. They play a fundamental role in enterprise environments and are widely adopted in sectors that require a high level of security, such as healthcare, finance, and government.
Apache Ranger Key Management Service (KMS)
Apache Ranger KMS is part of the Apache Ranger ecosystem that provides key management and encryption services to protect sensitive data in Hadoop clusters and related storage systems. It is an open-source tool designed to simplify cryptographic key management and ensure compliance with security policies and regulations.
Apache Ranger KMS is an important tool for organizations dealing with sensitive data in Hadoop clusters and distributed storage systems, helping to protect it through cryptographic key management and security policy enforcement. It plays a fundamental role in the Apache Ranger ecosystem and is widely used in Big Data environments.
Apache Ranger KMS Features
Among its main features, we highlight:
- Secure management of cryptographic keys;
- Integration with Hadoop systems and other storage systems;
- Policy-based access control for keys;
- Auditing and logging of key-related activities;
- Support for various encryption algorithms;
- Integration with Apache Ranger for security policy enforcement;
- Extensibility to support additional storage systems.
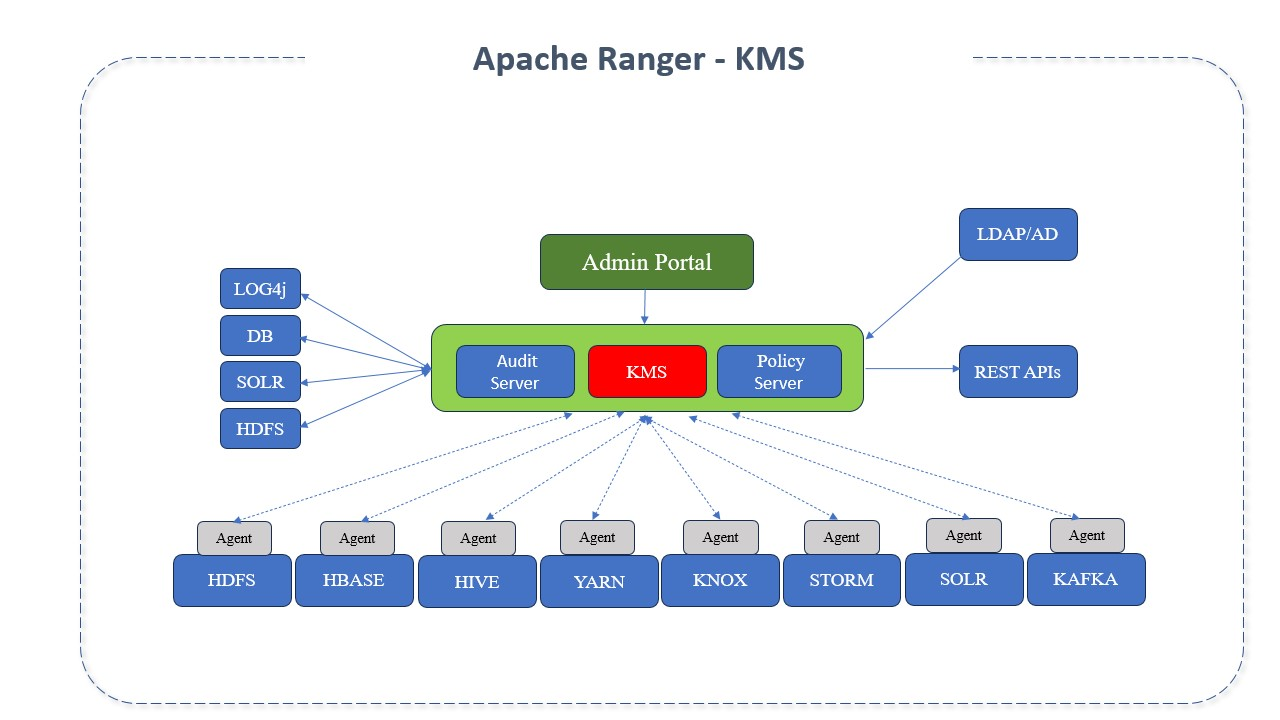
Apache Ranger KMS Architecture
The architecture of Apache Ranger KMS includes the following main components:
- Key Management Service: Central service that manages cryptographic keys;
- Key Database: Securely stores cryptographic keys;
- Policy Engine: Applies security policies to control access to keys;
- Audit Log: Records all key-related activities for audit purposes;
- Ranger Admin: The Apache Ranger administration interface for configuring security policies.
Apache Ranger KMS Resources
- Advanced Security: Strengthens data security by encrypting sensitive information.
- Facilitates Compliance: Simplifies compliance with data security regulations.
- Fine-grained Control: Provides more detailed control over who can access and manage cryptographic keys.
- Logging and Monitoring: Facilitates logging and monitoring of activities for auditing and compliance purposes.
- Easy Integration: Can be seamlessly integrated with Hadoop systems and other Big Data technologies.
Best Practices for Apache Ranger KMS
When using Apache Ranger KMS (Key Management Service) or any other cryptographic key management system, it is essential to follow security best practices to ensure adequate protection of the keys and the sensitive data they protect. Here are some best practices when using Apache Ranger KMS:
- Clear Security Policies: Define clear security policies that describe who has access to keys and under what conditions.
- Granular Access Control: Ensure that only authorized people and systems can access cryptographic keys.
- Regular Key Rotation: Establish policies for regular key rotation, ensuring that keys do not become obsolete and vulnerable.
- Activity Auditing: Enable activity auditing in Apache Ranger KMS to record and monitor all key-related operations.
- Physical and Logical Protection: Maintain a high level of physical and logical protection around Apache Ranger KMS components, including Hardware Security Modules (HSMs) if used.
- Updates and Patches: Keep Apache Ranger KMS updated with the latest security updates and patches to fix known vulnerabilities.
- Segregation of Duties: Implement segregation of duties to ensure that key management responsibilities are distributed among multiple people or teams.
- Continuous Monitoring: Establish a continuous monitoring system to detect suspicious or unauthorized key-related activities.
- Communication Encryption: Ensure that all communications between Apache Ranger KMS components are encrypted to protect data in transit.
- Training and Awareness: Provide adequate training to Apache Ranger KMS administrators and users to ensure correct and secure use of the system.
- Backup and Recovery: Implement backup and recovery policies to ensure that keys are not lost in case of system failure.
- Disaster Recovery Testing: Conduct regular disaster recovery tests to ensure you can restore keys in case of a major failure.
- Compliance with Regulations: Ensure that your Apache Ranger KMS usage practices comply with relevant data security regulations for your organization and industry.
- Periodic Policy Review: Conduct periodic reviews of security policies and update them as needed to meet the ever-evolving security needs.
- Least Privilege Access: Follow the principle of "least privilege access," granting access only to the keys and cryptographic information that users or systems need to perform their functions.
- Incident Management: Establish incident management procedures to effectively respond to any security breach or suspicious event.
- Vulnerability Assessment: Conduct regular vulnerability assessments to identify and mitigate potential security threats.
Remember that security best practices should be tailored to your organization's specific needs and applicable regulations. It is essential to stay up-to-date on security best practices and adjust your policies and procedures according to changes in the threat landscape.
Apache Ranger KMS Project Details
Apache Ranger KMS (Key Management Service) is primarily written in the Java programming language. The Apache ecosystem, of which Apache Ranger is a part, is largely based on Java, and this extends to the Apache Ranger KMS source code. The use of Java allows Apache Ranger KMS to run on various platforms and operating systems compatible with Java, making it highly portable and scalable.
Sources: